Solutions
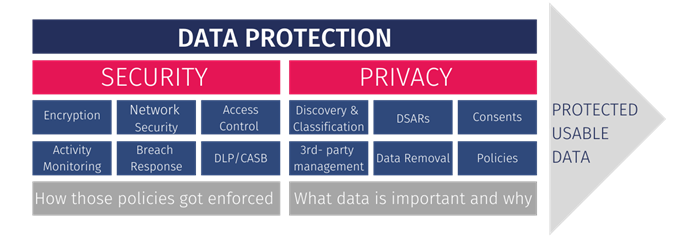
DATA SECURITY & PRIVACY
Data security protects information from unauthorized access, use, and disclosure. It also protects it from disruption, modification, or destruction. Data privacy is the right to control who gets to see sensitive personal information